ricodeniellecatherine
WHAT ARE THE OTHER NETWORK DEVICES?
These devices play crucial roles in enabling communication and interaction within a computer network. means "devices, other than the central processing system, having unique network addresses and capable of communicating over a network."
Working of Modem
The two main components of a modem are modulation and demodulation. Where the modem can perform both tasks simultaneously. The step-by-step working of the modem is given below:
Features of Modem
- Modems can modulate as well as demodulate the signals simultaneously.
- Modem allows to connect only a specific number of devices to the internet.
- According to the features of modem, it’s price ranges.
- Modems can be upgraded with the help of a specific software patch.
- To use the devices over the internet with a modem devices need to be configured with an Internet Service Provider(ISP).
- When the modem is connected to Hub it slows down its process.
Advantages of Modem
- A modem converts digital signals into an analog signal.
- The cost of a modem increases according to the features it has.
- The modem helps to connect the LAN to the internet.
- Modem performs both modulation and demodulation processes simultaneously
Disadvantages of Modem
- The working of the modem slows down when connected to the hub.
- The modem cannot track the traffic between the LAN and the internet.
- When using a modem a limited number of network devices can be connected to the internet.
- Modems have a high rock of security-related attacks.
- The modem does not provide maintenance of traffic.
Types of NIC Cards
NIC cards are of two types −
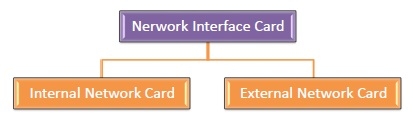
Internal Network Cards
In internal networks cards, motherboard has a slot for the network card where it can be inserted. It requires network cables to provide network access. Internal network cards are of two types. The first type uses Peripheral Component Interconnect (PCI) connection, while the second type uses Industry Standard Architecture (ISA).

External Network Cards
In desktops and laptops that do not have an internal NIC, external NICs are used. External network cards are of two types: Wireless and USB based. Wireless network card needs to be inserted into the motherboard, however no network cable is required to connect to the network. They are useful while traveling or accessing a wireless signal.
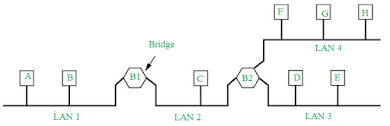
Network bridges are devices that allow multiple LANs to communicate with one another, expanding their reach beyond that of a single network. They inspect incoming traffic from network devices like computers, phones, printers, and routers, then decide whether to forward that traffic or discard it. There are seven layers to every network, from the hardware devices used to transmit information to applications. The Open Systems Interconnection (OSI) diagram maps these layers out visually. Network bridges are on the second, or data-link, layer of the OSI model.
Types of Bridges:
There are three types of bridges in computer networks, which are as follows:
- Transparent bridge
- Source routing bridge
- Translational bridge
Transparent Bridge:
Transparent bridges are invisible to other devices on the network. This bridge doesn’t reconfigure the network on the addition or deletion of any station. The prime function of the transparent bridge is to block or forward the data according to the MAC address.
Source Routing Bridge:
Source routing bridges were developed and designed by IBM specifically for token ring networks. The frame’s entire route is embedded with the data frames by the source station to perform the routing operation so that once the frame is forwarded it must follow a specific defined path/route.
Translational Bridge:
Translational bridges convert the received data from one networking system to another. Or it is used to communicate or transmit data between two different types of networking systems. Like if we are sending data from a token ring to an Ethernet cable, the translational cable will be used to connect both the networking system and transmit data.
Bridge in Computer Network:
A bridge in a computer network is a device used to connect multiple LANs together with a larger Local Area Network (LAN). The mechanism of network aggregation is known as bridging. The bridge is a physical or hardware device but operates at the OSI model’s data link layer and is also known as a layer of two switches.
The primary responsibility of a switch is to examine the incoming traffic and determine whether to filter or forward it. Basically, a bridge in computer networks is used to divide network connections into sections, now each section has separate bandwidth and a separate collision domain. Here bridge is used to improve network performance.
Advantages:
- Bridges can be used as a network extension like they can connect two network topologies together.
- It has a separate collision domain, which results in increased bandwidth.
- It can create a buffer when different MAC protocols are there for different segments.
- Highly reliable and maintainable. The network can be divided into multiple LAN segments.
Disadvantages:
- Expensive as compared to hubs and repeaters.
- Slow in speed.
- Poor performance as additional processing is required to view the MAC address of the device on the network.
- As the traffic received is in bulk or is broadcasted traffic, individual filtering of data is not possible.
- During the broadcasting of data, the network has high broadcast traffic and broadcast storms can be formed.
A firewall in a computer network provides security at the perimeter by monitoring incoming and outgoing data packets in network traffic for malware and anomalies. A firewall filters traffic as it attempts to enter and exit your network as opposed to antivirus software that scans devices and storage systems on the network for threats that have penetrated your defenses. A firewall is designed to follow a predefined set of security rules to determine what to allow on your network and what to block.
Depending on where it is deployed and its purpose, a firewall can be delivered as a hardware appliance, as software, or software as a service (SaaS). There are five main types of firewalls depending upon their operational method:
- stateless or packet filtering firewall
- stateful inspection firewall
- circuit-level gateway
- application-level gateway
- next-generation firewall (NGFW)
Stateless or Packet Filtering Firewall
A packet filtering firewall protects the network by analyzing traffic in the transport protocol layer where applications can communicate with each other using specific protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
The firewall examines the data packets at this layer, looking for malicious code that can infect the network or device. If a data packet is identified as a potential threat, the firewall rejects it. Small businesses that need basic protection from existing cyber threats can benefit from a packet-filtering firewall.
Packet-filtering firewalls analyze surface-level details only and do not open the packet to examine the actual data (content payload). They check each one in isolation for destination and IP address, packet type, port number, and network protocols but not in context with current traffic streams.
Stateful Inspection Firewall
Stateful inspection firewalls operate at the gateway between systems behind the firewall and resources outside the enterprise network. Stateful inspection firewalls are situated at Layers 3 and 4 of the Open Systems Interconnection (OSI) model.
State-aware firewalls examine each packet (stateful inspection), and track and monitor the state of active network connections while analyzing incoming traffic for potential risks. The “state” is the most recent or immediate status of a process or application.
Stateful firewalls can detect attempts by unauthorized individuals to access a network, as well as analyze the data within packets to see if they contain malicious code. They are very effective at defending the network against denial of service (DoS) attacks.
It is important to monitor the state and context of network communications because this information can be used to identify threats—either based on where they are coming from, where they are going, or the content of their data packets. This method offers more security than either packet filtering or circuit monitoring alone but exacts a greater toll on network performance.
Circuit-level Gateway
Circuit-level gateways operate at the session layer of the Open Systems Interconnection (OSI) model. In the OSI model, a handshake must occur before information can be passed from one cyber entity to another. Circuit-level gateways determine the security of an established connection between the transport layer and the application layer of the TCP/Internet Protocol (TCP/IP) stack by monitoring TCP handshakes between local and remote hosts.
While circuit-level gateways have minimal impact on network performance, a data packet containing malware can bypass a circuit-level gateway easily even if it has a legitimate TCP handshake. This is because circuit-level gateways do not filter the content in data packets. To fill this gap, circuit-level gateways are often paired with another type of firewall that performs content filtering.
Application-level Gateway
also referred to as a “proxy firewall,” serves as an intermediate between internal and external systems. An application-level gateway operates at the application layer, the highest of the OSI model. It employs deep packet inspection (DPI) on incoming traffic to check both data packet payloads (content) and headers. This firewall makes sure that only valid data exists at the application level before allowing it to pass through.
Application-level gateways follow a set of application-specific policies to determine which communications are allowed to pass to and from an application. They help protect a network by masking clients’ requests before sending them to the host.
When network anonymity is required, application-level gateways are often in play. They are ideal for securing web apps from bad actors (malicious intent).
Next-Generation Firewall (NGFW)
A next-generation firewall (NGFW) is the only type of firewall that provides the capabilities to protect modern businesses against emerging cyberthreats. As malware and threats have become more difficult to detect at the access point, NGFW security has evolved to span the network and monitor behavior and intent.
NGFWs provide functions like deep-packet inspection, intrusion prevention (IPS), advanced malware detection, application control, and provide overall network visibility through inspection of encrypted traffic. They can be found anywhere from an on-premises network edge to its internal boundaries, and can also be employed on public or private cloud networks.
NGFWs CPU-intensive capabilities include decryption at a very high-performance level, deep-packet inspection post decryption, detection of malicious URLs, identification of command-and-control activities, and download of malware and threat correlation. Due to these advanced security capabilities, NGFWs are critical for heavily regulated industries such as finance or healthcare and are often integrated with other security systems and SIEMs for end-to-end vigilance and reporting.
A software firewall or “host firewall” protects just one computer. Typically, host firewalls are packaged with the operating systems in home or personal devices. Software firewalls protect individual hosts from viruses and other malicious content.
The most common kind of software firewall can be found on most personal computers. The firewall works by inspecting data packets that flow to and from your device. It compares the information in the data packets against a list of threat signatures. If a data packet matches the profile of a known threat, it is discarded.
Infrequently, software firewalls are used in corporate settings to provide an added layer of protection. Software firewalls also can monitor different programs running on the host, while filtering inbound and outbound traffic. This provides granular control, enabling the firewall to allow communications to and from one program but prevent communications to and from another.
Because software firewalls run on one host (e.g., a server or another device), firewall software needs to be installed on each device requiring protection. As such, software-based firewalls consume some of their hosts’ CPU and RAM resources. Because software firewalls must be installed and maintained individually on each host, scalability is limited.
Hardware Firewalls and How They Protect the Network
Often referred to as “network firewalls,” hardware firewalls are appliances placed at the perimeter of the network or network segment as a first line of defense. A hardware-based network firewall acts as a secure gateway at the network perimeter. It protects all devices and traffic beyond a specific point on the network, enabling broad scalability. For this reason, hardware-based network firewalls are ideal for medium and large organizations looking to protect many devices.
Network firewalls function at OSI Layers 3 and 4, scanning traffic between external sources and the local area network (LAN), or traffic moving between different segments inside the network.
Network firewalls monitor traffic by performing deep packet inspection and packet filtering. If the content of a data packet does not meet previously selected criteria based on rules set by the network administrator or security team, the network firewall rejects and blocks that traffic.
Network firewalls require more knowledge to configure and manage than their software-based, host firewall counterparts.
5.TRANSCEIVER
Transceivers are mechanical devices that combine a radio transmitter and a radio receiver. It can both transmit and receive radio waves for communication purposes. The transceiver is part of the network input card in a local area network. It can both send and receive messages over the network wire. But some types of networks need a receiver that is outside the network. The transceiver is built into mobile devices that use wireless transmission, such as smartphones and cell phones. It is a combination of transmitter and receiver in a single term. It can do both, transmit and receive radio waves for communication purpose , with the help of an antenna.
Working of Transceiver
In a transceiver, the listener won’t hear the signals when the emitter sends them. The transmitter and receiver can be linked to the same antenna with the help of an electric switch. This keeps the emitter’s signal from hurting the receiver.
The transceiver generates a signal, which could be electrical optical, or radiofrequency, depending on the medium of communication. The signal is then subjected to modulation. The modulated signal is then sent out through an antenna or through a cable. At the receiving end, another transceiver is waiting to capture the incoming signal. Then finally the signal gets subjected to demodulation and transmitted data gets recovered and the data gets provided to system for further processing or display.
In a sort of transceiver that is characterized as having half-duplex capabilities, it is not feasible to acquire signals while the device is sending. Some of the transceivers, also known as duplexes, are intended to be able to receive signals at all stages of the transmission process. Both the transmitter and the receiver work at distinct frequencies, which prevents the signal from the transmitter from interfering with the signal from the reception. Phones that are cordless as well as cellular phones employ this mode of operation.
Transceiver Connection
Follow these steps to make a secure connection of Transceiver –
- Before installing, make sure that both the wire and the transmitter are clean.
- Take off any plugs that protect the device and wire.
- Place a cable so that the key, which is the ridge on one side of the cable connection, lines up with the transceiver’s hole.
- Put the wire into the transceiver until you hear the click of the locking device. There is only one way to plug in a cable because it has a key.
- If a wire does not go in easily, make sure it is facing the right way.
- Join the antenna to the radio receiver. Signal strength can be affected by the type of receiver and where it is placed.
- Set the receiver to the frequency or channel you want to use.
- Grounding the transmitter will keep it safe and reduce electrical interference, which is especially important for outdoor setups.
- To help you communicate through the transmitter, you can connect a microphone or a headset to it.
- After you have completed all the necessary setup steps, you can begin interacting with other transceiver users on the frequency or channel you have selected. Maintain the appropriate manners and standards for communicating.
Transceiver Structure and Design
A Wireless Transceiver should have these basic important blocks.
- Antenna or Antenna array
- Duplexer
- Transmitter section
- Receiver section
Antenna or Antenna array
Antenna array is made of similar antenna elements. So in order to transmit and receive signals one or more antennas are used. Transmitting antenna receives current and generate EM waves as output where they can be received by more antennas.
Duplexer
Isolating one segment from another that is connected at a single point allows for bidirectional communication to take place along a single channel without the need for additional connections. In a typical arrangement, the transmitter route in transceivers is partitioned off from the receiving portion. Such that the signal being broadcast does not cause interference with the segment being received.
Transmitter Section
In this stage, the signal at the base band is changed into the transmission signal so that it can satisfy the criteria of the subsequent wireless transmissions. Modulation, carrier mixing, and encoding are the fundamental procedures that need to be completed before the transmission can begin. To boost the power of the transmission signal, a power amplifier is utilized. The power of the signal is first amplified, and then it is transferred via the transmitter antenna.
Receiver Section
The receiver part includes a demodulator, a decoder, a low noise amplifier, and the antenna for the receiver. The signal that was received ought to have the necessary SNR value. The signal-to-noise ratio (SNR) of the transmitted signal drops due to the many events during transmission.
Types of Transceivers
Some of the types of Transceivers are as follows:
- RF Transceivers
- Fiber Optic Transceiver
- Ethernet Transceivers
- Wireless Transceivers
RF Transceivers (Radio Frequency)
A device known as a radio frequency (RF) transceiver can transmit and receive radio signals. A radio frequency (RF) transceiver combines the capabilities of a transmitter and a receiver into a single device. Common devices containing RF transceivers include citizens’ band radios, walkie-talkies, cordless phones, cellphones, and computers capable of using a wireless network
Fiber Optic Transceiver
Common other names for this product include optics module, optical module, and fiber optical transceiver. Fiber optic technology is used for data transmission in this gadget. Here, light sources like VSCELs, DFB lasers, and FPs can be used to send data.
Ethernet Transceivers
To send and receive data through a network, electrical gadgets and computers can be linked with the help of an Ethernet transceiver. Ethernet transceivers can also be called MAUs (media access units). Collision detection, digital data conversion, Ethernet interface processing, and network access are some of the primary roles of this transceiver.
Wireless Transceivers
The physical layer and the media access control layer are the two main functional layers of wireless transceivers. An RF front end and baseband processor make up the physical layer; the latter converts a bitstream into a sequence of symbols for transmission.
Advantages and Disadvantages of Transceivers
There are some list of Advantages and Disadvantages of Transceivers given below :
Advantages of Transceivers
- Cost-Efficiency: Transceivers can be more cost-effective than purchasing separate transmitter and receiver units, as they combine both functions into one device.
- Space Saving: They are often smaller and more compact than separate transmitter and receiver units.
- Reduced Complexity: Transceivers simplify circuitry and reduce the number of components needed.
- Energy Efficiency: Transceivers can be designed to switch between transmit and receive modes efficiently, saving power compared to running separate transmitter and receiver devices simultaneously.
Disadvantages of Transceivers
- Limited Simultaneous Use: Transceivers can generally either transmit or receive at a given moment, which means they may not be suitable for applications requiring continuous simultaneous two-way communication.
- Interference: Transmitting and receiving on the same device can introduce the potential for interference between the two functions, which can degrade signal quality.
- Complex Design: Depending on the required specifications, designing a transceiver that meets all performance criteria can be more complex than designing separate transmitter and receiver units.
- Limited Range: The combined functionality of a transceiver may result in limited transmission or reception range compared to separate specialized devices.





.jpg)








Comments
Post a Comment